

How to Detect and Prevent SIM Swapping Attacks Introduction SIM swapping has emerged as one of the most concerning cybersecurity threats in recent years. This sophisticated...


How to Secure Your Crypto Wallet Step-by-Step Introduction Cryptocurrency adoption continues to rise in 2025, with global crypto users now exceeding 750 million. Yet with this...


Legal Frameworks for Launching Security Tokens Security tokens represent a significant evolution in the world of blockchain and digital finance. They are digital assets that are...


Title: Implementing Zero-Knowledge Proofs in Web3 Applications Introduction In the rapidly evolving landscape of Web3, security and privacy are paramount. As blockchain technology continues to gain...


a brief overview of public vs private blockchain, the similarities between the two, along with the difference between public and private blockchain.
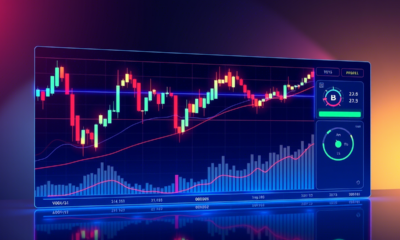
How to read crypto charts – a simple guide for beginners to read crypto charts and find key price levels


Ever wondered about the A to Z of NFTs? You’re not alone! Many friends have been curious about how to buy NFTs, where to buy NFTs,...
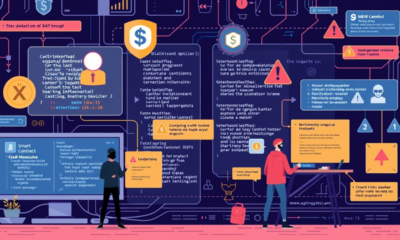



Introduction As the cryptocurrency space grows, security remains a top priority for individuals and organizations managing digital assets. Multi-signature wallets (multi-sig wallets) offer an advanced security...


Why Security Is Crucial in the World of Crypto The world of cryptocurrency offers immense opportunities for financial growth, innovation, and decentralization. However, with these benefits...